Programmers’ Digest 10/12/2022-10/19/2022: New Timing Attack Against NPM Redistry API, PoC Exploit Released for Critical Fortinet, Critical New Vulnerability in Apache Commons Text And More
1. New Timing Attack Against NPM Registry API Could Expose Private Packages
A novel timing attack discovered against the npm’s registry API can be exploited to potentially disclose private packages used by organizations, putting developers at risk of supply chain threats. By creating a list of possible package names, threat actors can detect organizations’ scoped private packages and then masquerade public packages, tricking employees and users into downloading them. The Scoped Confusion attack banks on analyzing the time it takes for the npm API (registry.npmjs[.]org) to return an HTTP 404 error message when querying for a private package, and measuring it against the response time for a non-existing module.
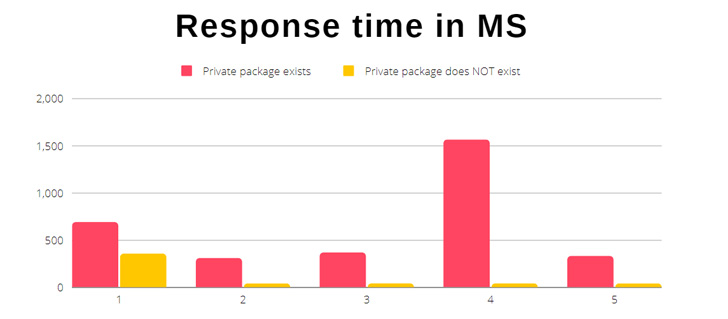
It takes on average less time to get a reply for a private package that does not exist compared to a private package that does. The idea, ultimately, is to identify packages internally used by companies, which could then be used by threat actors to create public versions of the same packages in an attempt to poison the software supply chain.
Recommendation
As preventive measures, it’s recommended that organizations routinely scan npm and other package management platforms for lookalike or spoofed packages that masquerade as the internal counterparts.
2. PoC Exploit Released for Critical Fortinet Auth Bypass Bug Under Active Attacks
A proof-of-concept (PoC) exploit code has been made available for the recently disclosed critical security flaw affecting Fortinet FortiOS, FortiProxy, and FortiSwitchManager, making it imperative that users move quickly to apply the patches. The issue, tracked as CVE-2022-40684 (CVSS score: 9.6), concerns an authentication bypass vulnerability that could allow a remote attacker to perform malicious operations on the administrative interface via specially crafted HTTP(S) requests. A successful exploitation of the shortcoming is tantamount to granting complete access “to do just about anything” on the affected system, including altering network configurations, adding malicious users, and intercepting network traffic.
That said, the cybersecurity firm said that there are two essential prerequisites when making such a request:
- Using the Forwarded header, an attacker is able to set the client_ip to “127.0.0.1”
- The “trusted access” authentication check verifies that the client_ip is “127.0.0.1” and the User-Agent is “Report Runner” both of which are under attacker control.
3. Zimbra Releases Patch for Actively Exploited Vulnerability in its Collaboration Suite
Zimbra has released patches to contain an actively exploited security flaw in its enterprise collaboration suite that could be leveraged to upload arbitrary files to vulnerable instances.
Tracked as CVE-2022-41352 (CVSS score: 9.8), the issue affects a component of the Zimbra suite called Amavis, an open source content filter, and more specifically, the cpio utility it uses to scan and extract archives. The flaw, in turn, is said to be rooted in another underlying vulnerability (CVE-2015-1197) that was first disclosed in early 2015, which according to Flashpoint was rectified, only to be subsequently reverted in later Linux distributions.
An attacker can use cpio package to gain incorrect access to any other user accounts.
Fixes are available in the following versions:
- Zimbra 9.0.0 Patch 27
- Zimbra 8.8.15 Patch 34
All an adversary seeking needs to do to weaponize the shortcoming is to send an email with a specially crafted TAR archive attachment that, upon being received, gets submitted to Amavis, which uses the cpio module to trigger the exploit.
4. Researchers Keep a Wary Eye on Critical New Vulnerability in Apache Commons Text
Researchers are closely tracking a critical, newly disclosed vulnerability in Apache Commons Text that gives unauthenticated attackers a way to execute code remotely on servers running applications with the affected component. The flaw (CVE-2022-42889) has been assigned a severity ranking of 9.8 out of a possible 10.0 on the CVSS scale and exists in versions 1.5 through 1.9 of Apache Commons Text. Proof-of-concept code for the vulnerability is already available, though so far there has been no sign of exploit activity. The Apache Software Foundation (ASF) released an updated version of the software (Apache Commons Text 1.10.0) on September 24 but issued an advisory on the flaw only last Thursday. In it, the Foundation described the flaw as stemming from insecure defaults when Apache Commons Text performs variable interpolation, which basically is the process of looking up and evaluating string values in code that contain placeholders. NIST, meanwhile, urged users to upgrade to Apache Commons Text 1.10.0, which it said, “disables the problematic interpolators by default.”
5. Feature-Rich ‘Alchimist’ Cyberattack Framework Targets Windows, Mac, Linux Environments
Researchers have uncovered a potentially dangerous cyberattack framework targeting Windows, Linux, and Mac systems that they assess is likely already being used in the wild. The framework consists of a new, stand-alone, command-and-control (C2) tool dubbed “Alchimist,” a previously unseen remote access Trojan (RAT) called “Insekt,” and several bespoke tools like a custom backdoor and malware for exploiting vulnerabilities in macOS. It also includes reverse proxies and several dual-use tools such as netcat, psexec, and an intranet-scanning tool called fscan.Alchimist is a new C2 framework that can be rapidly deployed and operated with relatively low technical expertise by a threat actor. It can generate a configured payload, establish remote sessions, deploy payloads to the remote machines, capture screenshots, perform remote shellcode execution and run arbitrary commands. Giving it those capabilities are a variety of malware tools, including a Mach-0 backdoor for macOS and a separate macOS malware dropper that exploits a known vulnerability in a root program associated with major Linux distributions (CVE-2021-4034).
6. Critical RCE Vulnerability Discovered in Popular Cobalt Strike Hacking Software
HelpSystems, the company behind the Cobalt Strike software platform, has released an out-of-band security update to address a remote code execution vulnerability that could allow an attacker to take control of targeted systems.
The post-exploitation tool consists of a team server, which functions as a command-and-control (C2) component, and a beacon, the default malware used to create a connection to the team server and drop next-stage payloads. The issue, tracked as CVE-2022-42948, affects Cobalt Strike version 4.7.1, and stems from an incomplete patch released on September 20, 2022, to rectify a cross-site scripting (XSS) vulnerability (CVE-2022-39197) that could lead to remote code execution. The XSS vulnerability could be triggered by manipulating some client-side UI input fields, by simulating a Cobalt Strike implant check-in or by hooking a Cobalt Strike implant running on a host. This means that a malicious actor could exploit this behavior by means of an HTML «object» tag, utilizing it to load a custom payload hosted on a remote server and inject it within the note field as well as the graphical file explorer menu in the Cobalt strike UI. However, it was found that remote code execution could be triggered in specific cases using the Java Swing framework, the graphical user interface toolkit that’s used to design Cobalt Strike.
7. Researchers Detail Windows Zero-Day Vulnerability Patched Last Month
Details have emerged about a now-patched security flaw in Windows Common Log File System (CLFS) that could be exploited by an attacker to gain elevated permissions on compromised machines. Tracked as CVE-2022-37969 (CVSS score: 7.8), the issue was addressed by Microsoft as part of its Patch Tuesday updates for September 2022, while also noting that it was being actively exploited in the wild. Now, the Zscaler ThreatLabz researcher team has disclosed that it captured an in-the-wild exploit for the then zero-day on September 2, 2022. The cause of the vulnerability is due to the lack of a strict bounds check on the field cbSymbolZone in the Base Record Header for the base log file (BLF) in CLFS.sys. If the field cbSymbolZone is set to an invalid offset, an out-of-bounds write will occur at the invalid offset. According to Zscaler, the vulnerability is rooted in a metadata block called base record that’s present in a base log file, which is generated when a log file is created using the CreateLogFile() function.
