Programmers’ Digest 10/26-11/02: Critical RCE Vulnerability, OpenSSL Releases Patch for 2 New High-Severity Vulnerabilities, Dropbox Breach, Critical VMware RCE Vulnerability And More
1. Critical RCE Vulnerability Reported in ConnectWise Server Backup Solution
IT service management software platform ConnectWise has released Software patches for a critical security vulnerability in Recover and R1Soft Server Backup Manager (SBM). The issue, characterized as a “neutralization of Special Elements in Output Used by a Downstream Component,” could be abused to result in the execution of remote code or disclosure of sensitive information. ConnectWise’s advisory notes that the flaw affects Recover v2.9.7 and earlier, as well as R1Soft SBM v6.16.3 and earlier, are impacted by the critical flaw. At its core, the issue is tied to an upstream authentication bypass vulnerability in the ZK open source Ajax web application framework (CVE-2022-36537), which was initially patched in May 2022. Affected ConnectWise Recover SBMs have automatically been updated to the latest version of Recover (v2.9.9). While there is no evidence of active exploitation of the vulnerability in the wild, a proof-of-concept shows that it can be abused to bypass authentication, gain remote code execution on SBM, and push LockBit 3.0 ransomware to all downstream endpoints.
2. OpenSSL Releases Patch for 2 New High-Severity Vulnerabilities
The OpenSSL project has rolled out fixes to contain two high-severity flaws in its widely used cryptography library that could result in a denial-of-service (DoS) and remote code execution. The issues, tracked as CVE-2022-3602 and CVE-2022-3786, have been described as buffer overrun vulnerabilities that can be triggered during X.509 certificate verification by supplying a specially-crafted email address. Versions 3.0.0 through 3.0.6 of the library are affected by the new flaws, which has been remediated in version 3.0.7. It’s worth noting that the commonly deployed OpenSSL 1.x versions are not vulnerable. While CVE-2022-3602 was initially treated as a Critical vulnerability, its severity has since been downgraded to High, citing stack overflow protections in modern platforms.
The OpenSSL Project further noted the bugs were introduced in OpenSSL 3.0.0 as part of punycode decoding functionality that’s currently used for processing email address name constraints in X.509 certificates. Despite the change in severity, OpenSSL said it considers “these issues to be serious vulnerabilities and affected users are encouraged to upgrade as soon as possible.”
3. Dropbox Breach: Hackers Unauthorizedly Accessed 130 GitHub Source Code Repositories
File hosting service Dropbox on Tuesday disclosed that it was the victim of a phishing campaign that allowed unidentified threat actors to gain unauthorized access to 130 of its source code repositories on GitHub. The breach resulted in the access of some API keys used by Dropbox developers as well as “a few thousand names and email addresses belonging to Dropbox employees, current and past customers, sales leads, and vendors.” It, however, stressed that the repositories did not contain source code related to its core apps or infrastructure.
The investigation has found that the code accessed by this threat actor contained some credentials—primarily, API keys—used by Dropbox developers. The successful breach resulted from a phishing attack that targeted multiple Dropbox employees using emails impersonating the CircleCI continuous integration and delivery platform and redirecting them to a phishing landing page where they were asked to enter their GitHub username and password. On the same phishing page, the employees were also asked to “use their hardware authentication key to pass a One Time Password (OTP).”
After stealing the Dropboxers’ credentials, the attackers gained access to one of Dropbox’s GitHub organizations and stole 130 of its code repositories.
4. Exploit Released For Critical VMware RCE Vulnerability, Patch Now
Proof-of-concept exploit code is now available for a pre-authentication remote code execution (RCE) vulnerability allowing attackers to execute arbitrary code remotely with root privileges on unpatched Cloud Foundation and NSX Manager appliances. The flaw (CVE-2021-39144) is in the XStream open-source library used by the two VMware products and was assigned an almost maximum CVSSv3 base score of 9.8/10 by VMware. Unauthenticated threat actors can exploit it remotely in low-complexity attacks that will not require user interaction. VMware released security updates to address the CVE-2021-39144 flaw . Additionally, because of the severity of the issue, the company also provided patches for some end-of-life products.
5. Microsoft Fixes Critical RCE Flaw Affecting Azure Cosmos DB
Analysts at Orca Security have found a critical vulnerability affecting Azure Cosmos DB that allowed unauthenticated read and write access to containers. Named CosMiss, the security issue is in Azure Cosmos DB built-in Jupyter Notebooks that integrate into the Azure portal and Azure Cosmos DB accounts for querying, analyzing, and visualizing NoSQL data and results easier. Azure Cosmos DB is Microsoft’s fully managed NoSQL database that features broad API type support for applications of all sizes. Jupyter Notebooks is a web-based interactive platform that allows users to access Cosmos DB data. The issue that researchers at Orca Security discovered is that Cosmos DB Jupyter Notebooks lacked authentication checks that prevented unauthorized access, and even modify a container, if they had the UUID of the Notebook Workspace.
6. New Open-Source Tool Scans Public AWS S3 Buckets For Secrets
A new open-source ‘S3crets Scanner’ scanner allows researchers and red-teamers to search for ‘secrets’ mistakenly stored in publicly exposed or company’s Amazon AWS S3 storage buckets. Amazon S3 (Simple Storage Service) is a cloud storage service commonly used by companies to store software, services, and data in containers known as buckets.
Unfortunately, companies sometimes fail to properly secure their S3 buckets and thus publicly expose stored data to the Internet. This type of misconfiguration has caused data breaches in the past, with threat actors gaining access to employee or customer details, backups, and other types of data.
During an exercise examining SEGA’s recent assets exposure, security researcher Eilon Harel discovered that no tools for scanning accidental data leaks exist, so he decided to create his own automated scanner and release it as an open-source tool on GitHub. To help with the timely discovery of exposed secrets on public S3 buckets, Harel created a Python tool named “S3crets Scanner”.
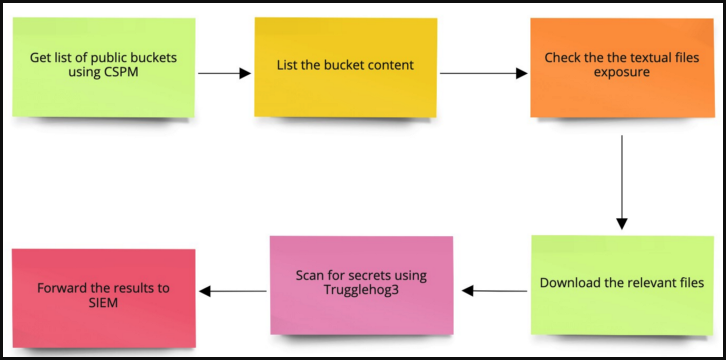
The scanner tool will only list S3 buckets that have the following configurations set to ‘False,’ meaning that exposure was likely accidental:
- “BlockPublicAcls”,
- “BlockPublicPolicy”,
- “IgnorePublicAcls”,
- “RestrictPublicBuckets”.
Any buckets that were intended to be public are filtered out from the list before the textual files are downloaded for the “secrets scanning” step. When scanning a bucket, the script will examine the content of text files using the Trufflehog3 tool, an improved Go-based version of the secrets scanner that can check for credentials and private keys on GitHub, GitLab, filesystems, and S3 buckets.
7. Microsoft fixes Windows vulnerable driver blocklist sync issue
Microsoft says it addressed an issue preventing the Windows kernel vulnerable driver blocklist from being synced to systems running older Windows versions. This blocklist (stored in the DriverSiPolicy.p7b file) is designed to block threat actors from dropping legitimate but vulnerable drivers on targets’ systems in Bring Your Own Vulnerable Driver (BYOVD) attacks on HVCI-enabled Windows machines or those running Windows in S Mode. The flawed drivers are then exploited to escalate privileges in the Windows kernel and execute malicious code, disabling security solutions and taking control of the device. Although Microsoft has been advertising its driver blocklist as capable of hardening Windows systems against vulnerable third-party drivers, ANALYGENCE security analyst Will Dormann found that wasn’t the case. As Dormann discovered, unlike Windows 11 devices, even up-to-date Windows 10 and Windows Server systems were being provided with an outdated list of vulnerable drivers from December 2019, exposing customers who thought they were protected to BYOVD attacks. Microsoft reluctantly acknowledged his findings and promised to address this issue and update its misleading online support docs.
