Programmers’ Digest 11/02-09/22: PyPIPackages Caught Dropping ‘W4sSP, Patches Issued for 6 Actively Exploited Zero-Days, Microsoft WinGet Package Manager Failing And More.
1. Dozens of PyPIPackages Caught Dropping ‘W4sSP’ Info-Stealing Malware.
Researchers have discovered over two dozen Python packages on the PyPI registry that are pushing info-stealing malware. Most of these contain obfuscated code that drops “W4SP” info-stealer on infected machines, while others make use of malware purportedly created for “educational purposes” only. The packages are typosquats—that is, threat actors publishing these have intentionally named them similar to known Python libraries in hopes that developers attempting to fetch the real library make a spelling error and inadvertently retrieve one of the malicious ones.
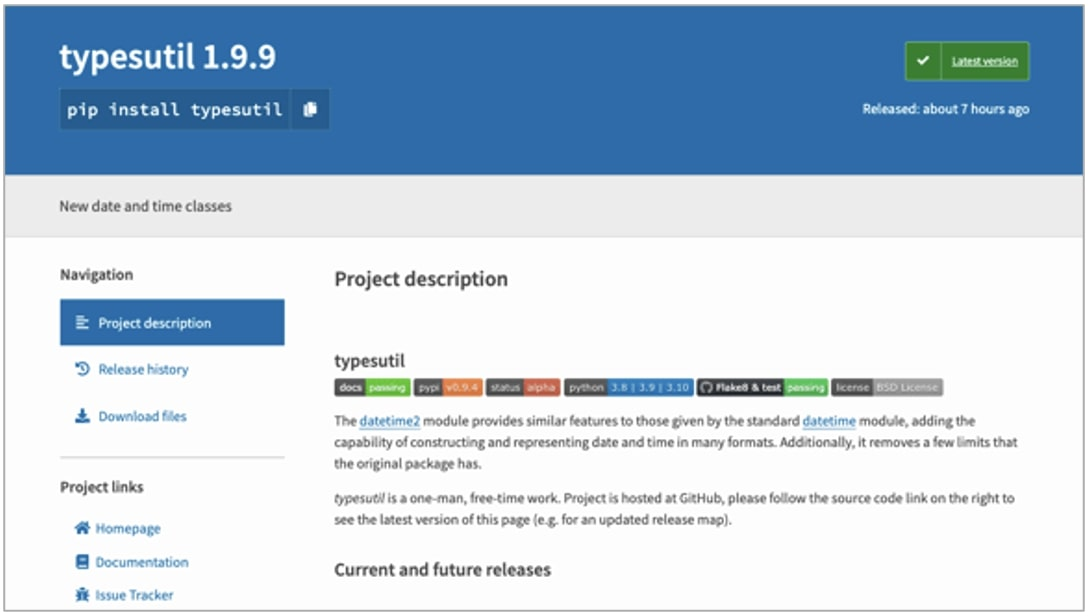
PyPI package ‘typesutil’ is one of the typosquats dropping W4SP infostealer
As an example, typesutil attack “starts by copying existing popular libraries and simply injecting a malicious __import__ statement into an otherwise healthy codebase,” write Phylum researchers. Ultimately, the malware dropped by these packages was W4SP Stealer that exfiltrates your Discord tokens, cookies and saved passwords. All of the packages put together have been downloaded over 5,700 times based on Pepy.tech stats.
2. Install Latest Windows Update ASAP! Patches Issued for 6 Actively Exploited Zero-Days.
Microsoft’s latest round of monthly security updates has been released with fixes for 68 vulnerabilities spanning its software portfolio, including patches for six actively exploited zero-days. 12 of the issues are rated Critical, two are rated High, and 55 are rated Important in severity. This also includes the weaknesses that were closed out by OpenSSL the previous week. Also separately addressed at the start of the month is an actively exploited flaw in Chromium-based browsers (CVE-2022-3723) that was plugged by Google as part of an out-of-band update late last month. Customers are advised to update their Exchange Server systems immediately, regardless of whether any previously recommended mitigation steps have been applied. The mitigation rules are no longer recommended once systems have been patched.
The list of actively exploited vulnerabilities, which allow privilege elevation and remote code execution, is as follows:
- CVE-2022-41040 (CVSS score: 8.8) – Microsoft Exchange Server Elevation of Privilege Vulnerability (aka ProxyNotShell);
- CVE-2022-41082 (CVSS score: 8.8) – Microsoft Exchange Server Elevation of Privilege Vulnerability (aka ProxyNotShell);
- CVE-2022-41128 (CVSS score: 8.8) – Windows Scripting Languages Remote Code Execution Vulnerability;
- CVE-2022-41125 (CVSS score: 7.8) – Windows CNG Key Isolation Service Elevation of Privilege Vulnerability.
3. Microsoft Fixes ProxyNotShell Exchange Zero-Days Exploited in Attacks/
Microsoft has released security updates to address two high-severity Microsoft Exchange zero-day vulnerabilities collectively known as ProxyNotShell and exploited in the wild. Tracked as CVE-2022-41082 and CVE-2022-41040, the two security bugs affect Microsoft Exchange Server 2013, 2016, and 2019. They enable attackers to escalate privileges to run PowerShell in the context of the system and gain arbitrary or remote code execution. Attackers have been chaining the two security flaws to deploy Chinese Chopper web shells on compromised servers for persistence and data theft, as well as for lateral movement in their victims’ networks since at least September 2022. As part of the November 2022 Patch Tuesday, Microsoft finally released security updates to address the two vulnerabilities. It is recommended that you install these updates immediately to be protected against these attacks.
4. VMware Fixes Three Critical Auth Bypass Bugs in Remote Access Tool.
VMware has released security updates to address three critical severity vulnerabilities in the Workspace ONE Assist solution that enable remote attackers to bypass authentication and elevate privileges to admin. The flaws are tracked as CVE-2022-31685 (authentication bypass), CVE-2022-31686 (broken authentication method), and CVE-2022-31687 (broken authentication control) and have received 9.8/10 CVSSv3 base scores. Non-authenticated threat actors can exploit them in low-complexity attacks that don’t require user interaction for privilege escalation. The company patched them with the release of Workspace ONE Assist 22.10 (89993) for Windows customers. VMware also patched a reflected cross-site scripting (XSS) vulnerability (CVE-2022-31688) that enables attackers to inject javascript code in the target user’s window and a session fixation vulnerability (CVE-2022-31689) that allows authentication after obtaining a valid session token.
5. Citrix Urges Admins to Patch Critical ADC, Gateway Auth Bypass.
Citrix is urging customers to install security updates for a critical authentication bypass vulnerability in Citrix ADC and Citrix Gateway. Under specific configurations, the three vulnerabilities can enable attackers to gain unauthorized access to the device, perform remote desktop takeover, or bypass the login brute force protection. Citrix ADC is a load-balancing solution for cloud applications deployed in the enterprise, ensuring uninterrupted availability and optimal performance.The three vulnerabilities affecting both Citrix Gateway and Citrix ADC are the following: CVE-2022-27510; CVE-2022-27513; CVE-2022-27516. Affected customers of Citrix ADC and Citrix Gateway are recommended to install the relevant updated versions of Citrix ADC or Citrix Gateway as soon as possible.
6. Microsoft WinGet Package Manager Failing Due to CDN Issues.
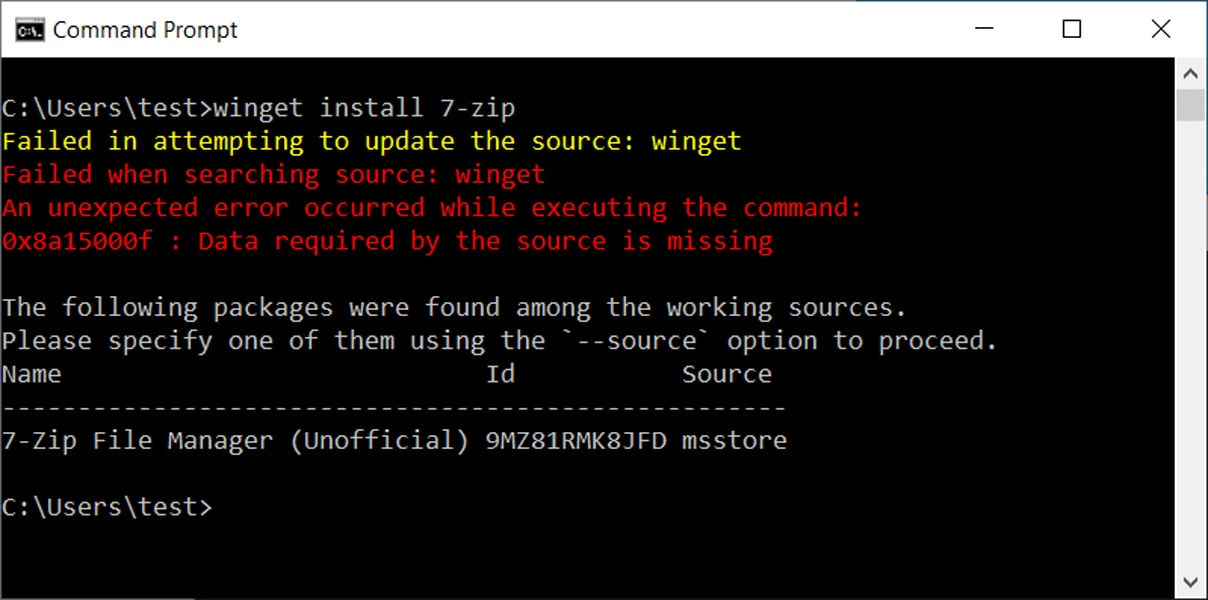
Microsoft’s WinGet package manager is currently having problems installing or upgrading packages due to the Azure Content Delivery Network (CDN) returning a 0-byte database file. Starting over the weekend, Windows users began reporting that when they attempted to install or upgrade apps using WinGet, they would receive different errors depending on the operation. For example, winget upgrade would display an error stating, “Failed in attempting to update the source: «winget» and winget install
WinGet displaying error
Windows users posted in a GitHub issue that the problem appears to be a CDN issue causing a zero-byte file to be sent back rather than the complete index of available applications. Like other package managers, WinGet uses a default repository to retrieve the available packages, which for WinGet is located at https://cdn.winget.microsoft.com/cache/source.msix. Microsoft Product Manager Demitrius Nelon has confirmed that they are suffering a CDN issue causing these errors for certain users. If you are using WinGet, your best bet is to wait for Microsoft to fix the CDN issue, and the package manager should automatically begin working again.
7. RomCom RAT Malware Campaign Impersonates KeePass, SolarWinds NPM, Veeam.
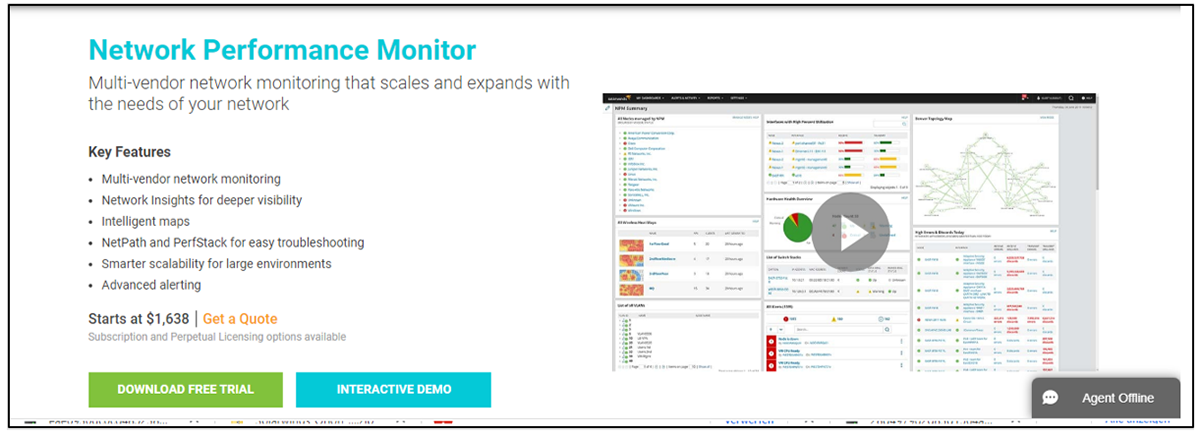
The threat actor behind the RomCom RAT (remote access trojan) has refreshed its attack vector and is now abusing well-known software brands for distribution. In a new campaign discovered by BlackBerry, the RomCom threat actors were found creating websites that clone official download portals for SolarWinds Network Performance Monitor (NPM), KeePass password manager, and PDF Reader Pro, essentially disguising the malware as legitimate programs.
The website that impersonates SolarWinds NPM delivers a trojanized version of the free trial and even links to an actual SolarWinds registration form that, if filled out by the victim, leads to being contacted by a real customer support agent.
The spoofed Solarwinds website
The downloaded app, though, has been modified to include a malicious DLL that downloads and runs a copy of the RomCom RAT from the “C:\Users\user\AppData\Local\Temp\winver.dll” folder. It is unclear at this time how the threat actors are luring potential victims to the sites, but it could be through phishing, SEO poisoning, or forum/social media posts.
8. Researchers Are Poisoning Open-Source Packages. What Should We do?
In the field of open-source security, researchers often publish malicious packages or poison existing ones with malicious code. These proofs of concepts (POCs) are done in an attempt to verify whether an attacker with malicious intent would be able to cause similar damage — or worse. However, while performing these actions, security researchers should adhere to several guidelines that will enable them to complete their research while keeping the ecosystem safe and clean to the maximum extent possible.
In the article, Aviad Gershon analyzes malicious packages containing ransomware scripts. He concludes that security professionals need to adhere to certain guidelines while conducting their research, which among others, include the following:
- Do No Harm — refrain from breaking existing components.
- Transparency — declare our activity “for research purposes” to anyone who may encounter it.
- Discretion — avoid collecting or revealing sensitive data of other parties.
