Programmers’ Digest #06
1. Researchers Uncover PyPI Package Hiding Malicious Code Behind Image File
A malicious package discovered on the Python Package Index (PyPI) has been found employing a steganographic trick to conceal malicious code within image files. The package in question, named “apicolor,” was uploaded to the Python third-party repository on October 31, 2022, and described as a “Core lib for REST API”. Apicolor, like other rogue packages detected recently, harbors its malicious behavior in the setup script used to specify metadata associated with the package, such as its dependencies. This takes the form of a second package called “judyb” as well as a seemingly harmless PNG file (“8F4D2uF.png”) hosted on Imgur, an image-sharing service.
The judyb code turned out to be a steganography module, responsible [for] hiding and revealing hidden messages inside pictures. The attack chain entails using the judyb package to extract obfuscated Python code embedded within the downloaded image, which, upon decoding, is designed to retrieve and execute a malicious binary from a remote server.
2. Researchers Reported Critical SQLi and Access Flaws in Zendesk Analytics Service
Cybersecurity researchers have disclosed details of now-patched flaws in Zendesk Explore that could have been exploited by an attacker to gain unauthorized access to information from customer accounts that have the feature turned on. The cybersecurity firm said there was no evidence to suggest that the issues were actively exploited in real-world attacks. According to the security software company, exploitation of the shortcoming first requires an attacker to register for the ticketing service of its victim’s Zendesk account as a new external user, a feature that’s likely enabled by default to allow end-users to submit support tickets. The vulnerability relates to an SQL injection in its GraphQL API that could be abused to exfiltrate all information stored in the database as an admin user, including email addresses, tickets, and conversations with live agents. A second flaw concerns a logic access issue associated with a query execution API, which was configured to run the queries without checking if the “user” making the call had adequate permission to do so.
3. Critical RCE Flaw Reported in Spotify’s Backstage Software Catalog and Developer Platform
Spotify’s Backstage has been discovered as vulnerable to a severe security flaw that could be exploited to gain remote code execution by leveraging a recently disclosed bug in a third-party module. The vulnerability (CVSS score: 9.8), at its core, takes advantage of a critical sandbox escape in vm2, a popular JavaScript sandbox library (CVE-2022-36067 aka Sandbreak), that came to light last month. An unauthenticated threat actor can execute arbitrary system commands on a Backstage application by exploiting a vm2 sandbox escape in the Scaffolder core plugin. According to Oxeye, the flaw is rooted in a tool called software templates that can be used to create components within Backstage.
While the template engine utilizes vm2 to mitigate the risk associated with running untrusted code, the sandbox escape flaw in the latter made it possible to execute arbitrary system commands outside of the security perimeter.
4. Multiple High-Severity Flaws Affect Widely Used OpenLiteSpeed Web Server Software
Multiple high-severity flaws have been uncovered in the open source OpenLiteSpeed Web Server as well as its enterprise variant that could be weaponized to achieve remote code execution. By chaining and exploiting the vulnerabilities, adversaries could compromise the web server and gain fully privileged remote code execution. The first of the three flaws is a directory traversal flaw (CVE-2022-0072, CVSS score: 5.8), which could be exploited to access forbidden files in the web root directory. The remaining two vulnerabilities (CVE-2022-0073 and CVE-2022-0074, CVSS scores: 8.8) relate to a case of privilege escalation and command injection, respectively, that could be chained to achieve privileged code execution. A threat actor who managed to gain the credentials to the dashboard, whether by brute-force attacks or social engineering, could exploit the vulnerability in order to execute code on the server. Multiple versions of OpenLiteSpeed (from 1.5.11 up to 1.7.16) and LiteSpeed (from 5.4.6 up to 6.0.11) are impacted by the issues, which have been addressed in versions 1.7.16.1 and 6.0.12 following responsible disclosure on October 4, 2022.
5. Over 15,000 WordPress Sites Compromised in Malicious SEO Campaign
A new malicious campaign has compromised over 15,000 WordPress websites in an attempt to redirect visitors to bogus Q&A portals. These malicious redirects appear to be designed to increase the authority of the attacker’s sites for search engines. The search engine poisoning technique is designed to promote a “handful of fake low quality Q&A sites” that share similar website-building templates and are operated by the same threat actor. A notable aspect of the campaign is the ability of the hackers to modify over 100 files per website on average, an approach that contrasts dramatically from other attacks of this kind wherein only a limited number of files are tampered with to reduce footprint and escape detection. This extensive compromise allows the malware to execute the redirects to websites of the attacker’s choice. The ultimate goal of the campaign is to “drive more traffic to their fake sites” and “boost the sites’ authority using fake search result clicks to make Google rank them better so that they get more real organic search traffic.”
6. Worok Hackers Abuse Dropbox API to Exfiltrate Data via Backdoor Hidden in Images
A recently discovered cyber espionage group dubbed Worok has been found hiding malware in seemingly innocuous image files, corroborating a crucial link in the threat actor’s infection chain. Czech cybersecurity firm Avast said the purpose of the PNG files is to conceal a payload that’s used to facilitate information theft. The Slovak cybersecurity company also documented Worok’s compromise sequence, which makes use of a C++-based loader called CLRLoad to pave the way for an unknown PowerShell script embedded within PNG images, a technique known as steganography. That said, the initial attack vector remains unknown as yet, although certain intrusions have entailed the use of ProxyShell vulnerabilities in Microsoft Exchange Server to deploy the malware.
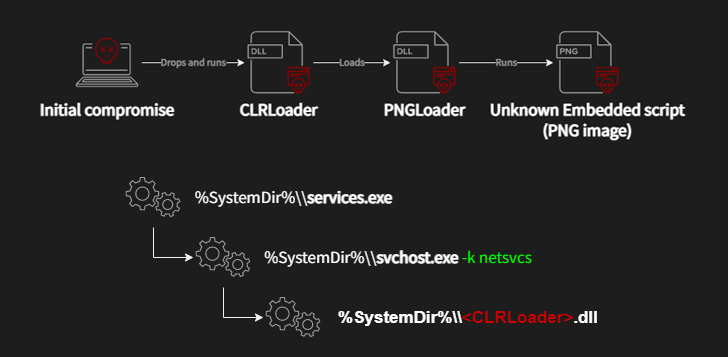
Avast’s findings show that the adversarial collective makes use of DLL side-loading upon gaining initial access to execute the CLRLoad malware. PNGLoad, which is launched by CLRLoad, is said to come in two variants, each responsible for decoding the malicious code within the image to launch either a PowerShell script or a .NET C#-based payload.
7. Citrix Issues Patches for Critical Flaw Affecting ADC and Gateway Products
Citrix has released security updates to address a critical authentication bypass flaw in the application delivery controller (ADC) and Gateway products that could be exploited to take control of affected systems.
Successful exploitation of the issues could enable an adversary to gain authorized access, perform remote desktop takeover, and even circumvent defenses against login brute-force attempts under specific configurations.
- CVE-2022-27510 – Unauthorized access to Gateway user capabilities;
- CVE-2022-27513 – Remote desktop takeover via phishing;
- CVE-2022-27516 – User login brute-force protection functionality bypass.
Exploitation, however, banks on the prerequisite that the appliances are either configured as a VPN (Gateway) or, alternatively, an authentication, authorization and accounting (AAA) virtual server in the case of CVE-2022-27516. One top of that, CVE-2022-27513 and CVE-2022-27516 also apply only when the RDP proxy feature and the user lockout functionality “Max Login Attempts” are set up, respectively.
